Public Key Infrastructure
Published on Aug 15, 2016
Abstract
Public Key Infrastructure is a system for supporting digital signatures and document encryption for an organization. It is fast becoming essential for an effective secure commerce and to fulfill general security and authentication requirements over non-secure networks (like the Net).
The banking services are the most popular usage of this technology, which is quickly spreading over all the applications that need security to be fully operational. The public keys must be stored in a directory, to ensure their worldwide availability. As they are accessible via unsecured networks (Internet), an infrastructure must be set-up to allow them to be undoubtedly trusted. This is the main objective of the Public Key Infrastructure.
Introduction of Public Key Infrastructure
The initial procedures used to certify the user's public keys are the most important, since a successful "masquerade" attempt during this phase may be difficult to subsequently detect. This may be done automatically by "internal" PKIs (runned by a company for its employees), but in the other cases it may require "face-to-face" authentication by either the CA or the RA, and even some "real" (or physical) document validation, like passports or identity cards
A certificate contains (at least) the basic information needed to provide a third party entity with the subject's public key:
. Subject Identification information
. Subject public Key
. CA Identification Information
. Validity (e.g. time)
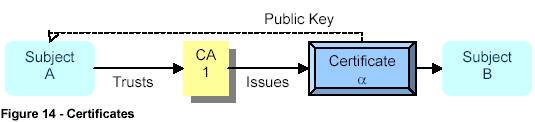
The certificates may be used to identify an entity - the identity certificates - or non-entities , such as permissions or credentials - the credential certificates. A true certificate is trusted to identify the subject and its public key or credentials and may then be used by other subjects.
Deliberate plagiarism is done when a person’s self esteem is very low. The person, therefore, actually steals the property of somebody else and claims it to be his own. He might also hire somebody to do his work. Accidental plagiarism is done when somebody unknowingly cites a phrase or copies words without acknowledging the author of the material
Certification Path:
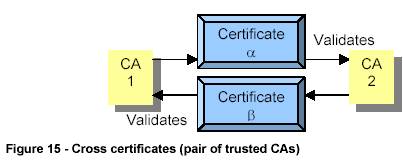
In a universe composed of several different CAs (and in which not all of them are connected to each other via a cross-certification) an arbitrary number of CAs must validate each other, until a certificate is obtained. This process is called certification path validation .
In the example above, the subject A needs the public key from the subject B. As the subject A does not "trust" the CA 3 (at least not directly), it needs to use the CA1, who "trusts" the CA2, who trusts CA3. This one knows the public key from the subject B that is then sent to the subject A
The CA relationships of a PKI govern its scalability. For a PKI to operate globally, its functions must scale up to a large number of users while keeping the size of the certification paths acceptable. Depending on the general relationships among their subjects, the CAs of a PKI may be arranged within a general hierarchy, top-down hierarchy or a web of trust
Some PKIs have no structure at all, depending exclusively on the cross-path certificates between the CAs. This structure may be called a "Web of Trust" - because each CA must base its trust on the certificates of other CAs - and is used by the PGP program. The users exchange keys and sign each others keys to establish a trust relationship
To increase the security, the private keys may be stored in Smartcards (something that the subject possesses). The CA root private keys must be strongly protected (if they are compromised the whole PKI is lost) and for ultimate security should ideally be stored in special hardware devices, which are tamperproof, climate proof and that may destroy the key in case of attack