Steganalysis
Published on Nov 23, 2015
Abstract
Steganography and steganalysis are important topics in information hiding. Steganography refers to the technology of hiding data into digital media without drawing any suspicion, while steganalysis is the art of detecting the presence of steganography.
Steganalysis is a relatively new branch of research. While steganography deals with techniques for hiding information, the goal of steganalysis is to detect and/or estimate potentially hidden information from observed data with little or no knowledge about the steganography algorithm or its parameters. It is fair to say that steganalysis is both an art and a science.
The art of steganalysis plays a major role in the selection of features or characteristics a typical stego message might exhibit, while the science helps in reliably testing the selected features for the presence of hidden information. Steganalysis has gained prominence in national security and forensic sciences since detection of hidden messages can lead to the prevention of disastrous security incidents. Steganalysis is a very challenging field because of the scarcity of knowledge about the specific characteristics of the cover media (an image, an audio or video file) that can be exploited to hide information and detect the same. The approaches adopted for steganalysis also sometimes depend on the underlying steganography algorithm(s) used.
Steganalysis is an art of deterring covert communications while avoiding affecting the innocent ones. Its basic requirement is to determine accurately whether a secret message is hidden in the testing medium [1]. Further requirements may include judging the type of the steganography, estimating the rough length of the message, or even extracting the hidden message. Steganography and steganalysis are in a hide-and-seek game [5].
They try to defeat each other and also develop with each other. Based on the medium used in steganography to embed the message are classified basically in three types, image steganography, audio steganography and video steganography. Digital images have high degree of redundancy in representation and pervasive applications in daily life, thus appealing for hiding data. As a result, the past decade has seen growing interests in researches on image steganography and image steganalysis
Motivation
Image steganalysis is the science of analyzing images to discover methods of detecting hidden messages and data within the images. On the steganography side, this is important in order to find methods in order to improve the algorithm implementing steganography. By exposing the flaws to the algorithm, the user can further improve the algorithm in order to make difficult to detect whether or not data is hidden in the images. Steganalysis is also especially important in security aspects, namely monitoring a user‟s communication with the outside world. In the age of internet, images are sent via email or by posting on websites.
Detecting whether or not data is hidden in the images will allow the monitor to further analyze the suspicious in order to find what the hidden message is. Steganalysis is very important to international security, as growing interest emerges as to whether terrorist organizations use steganographic techniques to communicate with each other. In fact steganalysis is taken so seriously with security aspects.
Types of Steganalysis
Based on the ultimate outcome of the effort we can classify steganalysis into two categories
Passive steganalysis:
Detect presence/absence of hidden message in a stego signal, identify the stego embedding algorithm.
Active steganalysis:
Estimate the embedded message length, estimate locations of the hidden message, estimate the secret key used in embedding, estimate some parameters of the stego embedding algorithm and extract the hidden message. In this report methods are described for image steganalysis and of passive type.
Basic Model
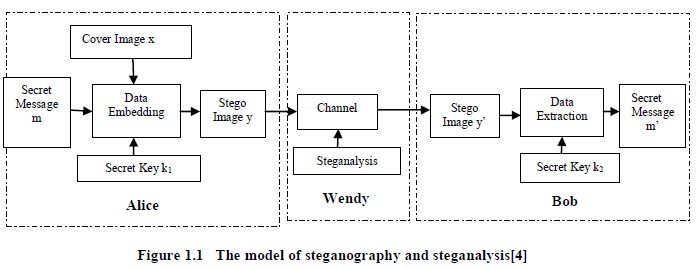
The issue in steganography and steganalysis is often modeled by the prisoner's problem [4] which involves three parties, as illustrated in figure 1.1. Alice and Bob are two prisoners who collaborate to hatch an escape plan while their communications will be monitored by a warden, Wendy. Using a data embedding method Ψ (.), secret information m is supposed to be hidden into a cover medium X by Alice with a key k1. Generation of an innocuous-looking stego medium Y can be described as Y=(X, m, k1). On the receiver's side, the medium obtained by Bob, denoted by Y’, is passed to a data extraction method Φ (.) to extract information m’ with a key k2. The extraction process may be described as m’ = Φ(Y’, k2).
The steganographic scheme should ensure m’= m. Although the public key steganographic scheme is considered in some literatures, the private key steganographic scheme, where k1 = k2 is assumed, remains the most common scenario in a steganographic system. Wendy can be active or passive judging from the nature of her work on examining the media in transmission. If she makes Y ’≠ Y in order to foil all possible covert communications between Alice and Bob, she is called an active warden. If she only takes actions when Y is found suspicious, she is a passive warden. In the passive warden case, which is the main focus of this report, once Wendy can differentiate Y from X; the steganographic method is considered broken. Note that this model only aims to explain the concepts of steganography and steganalysis, but not to detail the way on how to conduct the practice.
Criteria for Steganography
Three common requirements, security, capacity, and imperceptibility, may be used to rate the performance of steganographic techniques
Security:
Steganography may suffer from many active or passive attacks, correspondingly in the prisoner's problem when Wendy acts as an active or passive warden. If the existence of the secret message can only be estimated with a probability not higher than random guessing in the presence of some steganalytic systems, steganography may be considered secure under such steganalytic systems. Otherwise we may claim it to be insecure.
Capacity:
To be useful in conveying secret message, the hiding capacity provided by steganography should be as high as possible, which may be given in absolute measurement (such as the size of secret message), or in relative value (called data embedding rate, such as bits per pixel, bits per nonzero DCT coefficient, or the ratio of the secret message to the cover medium, etc.).
Imperceptibility:
Stego images should not have severe visual artifacts. If the resultant stego image appears innocuous enough, one can believe this requirement to be satisfied well for the warden not having the original cover image to compare.
Criteria for Steganalysis
The main goal of steganalysis is to identify whether or not a suspected medium is embedded with secret data, in other words, to determine the testing medium belong to the cover class or the stego class. If a certain steganalytic method is used to steganalyze a suspicious medium, there are four possible resultant situations .
True positive (TP): meaning that a stego medium is correctly classified as stego.
False negative (FN): meaning that a stego medium is wrongly classified as cover.
True negative (TN): meaning that a cover medium is correctly classified as cover.
False positive (FP): meaning that a cover medium is wrongly classified as stego.
LSB Steganalysis
LSB steganography can be done by replacing the LSBs by of randomly selected pixels in the cover image with the secret message bits. The selection of pixels may be determined by a secret key. In [6] auther has developed Steganalysis algorithm base on RGB to HSI colour model conversion. It is tested for stego-image database which is obtained by implementing various RGB Least Significant Bit Steganographic algorithms.
There are three different types of colour models they are HSI, HSV, and RGB. Any colour model can be converted to other model using mathematical expression In HSI model the values of Hue, Saturation and Intensity values are derived from all the three R, G and B values. Any change in the values of red or green or blue are easily reflected in all values of HSI colour model. RGB to HSI colour model can be mathematically derived with respect to normalized values of RGB
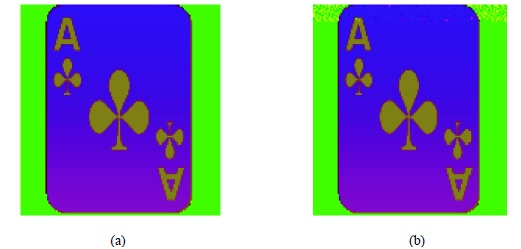
The Original and Stego-Image of Ace picture is shown in RGB Colour Model in figure 2.2 where from visual perception it‟s difficult to differentiate the Cover and Stego-Image. The same figures when converted to HSI Colour Model the visual distortion is seen in the top rows of Aces Stego-Image and it shown in figure 2.3. The proposed method was tested only for stego-images generated by LSB Steganography algorithm. Input images from various categories such as natural sceneries, birds, animals etc have chosen. Images generated from their own Stego Image Generator (SIG) tool was given as input.
Conclusion and Future Scope
This concept describes a novel methodology for recovering the cardiac pulse rate from video recordings of the human face and implementation using a simple webcam with ambient daylight providing illumination. This is the first demonstration of a low-cost method for non-contact heart rate measurements that is automated and motion-tolerant. Moreover, this approach is easily scalable for simultaneous assessment of multiple people in front of a camera. Given the low cost and widespread availability of webcams, this technology is promising for extending and improving access to medical care.
Although this concept only addressed the recovery of the cardiac pulse rate, many other important physiological parameters such as respiratory rate, heart rate variability and arterial blood oxygen saturation can potentially be estimated using the proposed technique. Creating a real-time, multi parameter physiological measurement platform based on this technology will be the subject of future work.
Improving Steganographic Security
There are some factors that may influence the steganographic security, such as the number of changed pixels/coefficients, the properties of cover images, etc. In the following some techniques are discussed for making the steganography less detectable
Increasing the Embedding efficiency:
If cover images do not need to be modified at all for conveying secret information, certainly the warden cannot di erentiate the cover images and stego images. Therefore, if the probability of modification to the images is less, the embedding changes to the image will reduce, and the security of the steganographic method may increase. Defining the embedding efficiency as the number of embedded bits per one embedding change. Hence, increasing the embedding efficiency is a possible way to enhance the steganographic security.
Reducing the Embedding Distortion:
Increasing the embedding efficiency can reduce the embedding changes to the image. However, it cannot guarantee that the distortion to the image is minimized. If not all of the coefficients are used for carrying data, Alice has the freedom to select the coefficients whose resultant distortions after data embedding are the smallest for modification. In this way, the stego image will be close to the cover image perceptually and statistically, thus enhancing the steganographic security.
Selecting Proper Cover Images:
In some scenarios, Alice has the freedom to select the most unsuspicious stego images for conveying secret information. The better images can be chosen according to the availability of the knowledge of a potential steganalyzer.
References
[1] Philip Bateman, “Image Steganography and Steganalysis”, Thesis of Master of Science in Security Technologies & Applications, University of Surrey, United Kingdom, August 2008.
[2] Qingxiao Guan, Jing Dong, and Tieniu Tan, “An Effective Image Steganalysis Method Based on Neighborhood Information of Pixels”, 18th IEEE International Conference on Image Processing , 2011.
[3] R. Chandramouli, “A mathematical framework for active steganalysis”, Springer Multimedia Systems, vol. 9, pp. 303–311, 2003.
[4] Bin Li, Junhui He, Jiwu Huang, Yun Qing Shi, “A Survey on Image Steganography and Steganalysis”, International Journal of Information Hiding and Multimedia Signal Processing Vol. 2, No. 2, April 2011.